Protecting Your IoT Devices and Deployments.
IoT authentication is a vital aspect of securing your IoT devices. Through IoT Connect, we offer several features and policies that can help you connect and monitor your IoT devices while ensuring maximum security.
IoT Connect offers a highly secure infrastructure with virtual private networks (VPNs) and additional services to ensure maximum security.
IoT Connect provides secure connectivity for IoT devices, including remote monitoring and management. We use VPNs and different types of APNs to establish secure connections between your data center and the Telenor IoT platform.
A Virtual Private Network (VPN) protects the transfer of information through the internet and increases the security of the connected product.
A VPN creates a secure connection between your data center and the connected products.
Our platform provides a secure connection through Virtual Private Networks (VPNs) between your data center and the Telenor IoT platform. We offer VPN tunnels that can be set up in your data center, or you can choose a Telenor IoT router that is ready to be plugged in. Our platform is interconnected across our core network, ensuring geographical redundancy.
Select between a Single VPN and Redundant VPN, that adds extra robustness.
Overview of redundant VPN setup with Telenor IoT provided end-points:
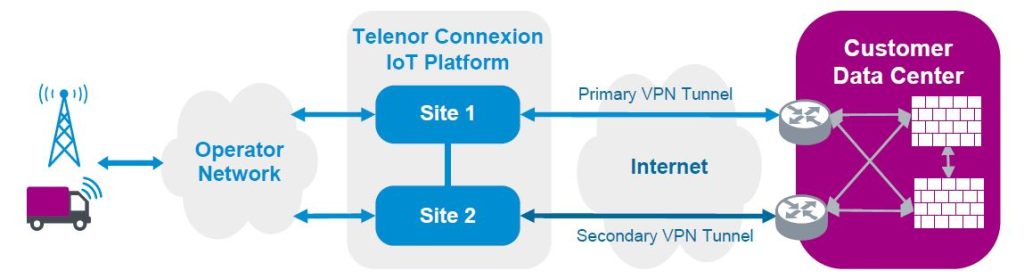
VPN tunnels are created over the internet that encapsulates the traffic. To set up a tunnel, an endpoint is needed in your data center.
There are two end-point options:
Explore how to use different types of APNs and VPN to meet specific technical requirements. We go through some concrete use cases to discover what differs between the types of APN and when they are to be used.
This video, produced in September 2022, showcases the product features that were available at that time.
Telenor IoT, our solutions and services are fully compliant with the latest requirements of GDPR and ISO 27001, ensuring that your data is protected, and your organization meets the latest legal regulations. We utilize the expertise of Telenor Group’s large security and architecture team to provide security by design.
Telenor IoT also offer black and whitelisting to provide maximum control over your network traffic. Our remote access self-service portal enables you to manage access rights to deployed IoT devices, administer user groups, and manage other related policies. Telenor IoT offer device security monitoring through our Service Operations Centre, providing proactive and robust defense against cyber-attacks. These steps give enterprise customers peace of mind to focus on their core business activities.
Ready to simplify your IoT deployment? Talk to our connectivity experts!



We’re proud to work with enterprises across the globe, transforming businesses and enabling new opportunities. Explore how industry leaders are achieving success with Telenor IoT.




